Pro-active monitoring of IAM policies provisioned through Terraform
We provision access to GCP services (like GCS buckets, BigQuery datasets) through Terraform very frequently. Access is provisioned to both Azure AD groups (synced to GCP) and GCP service accounts.
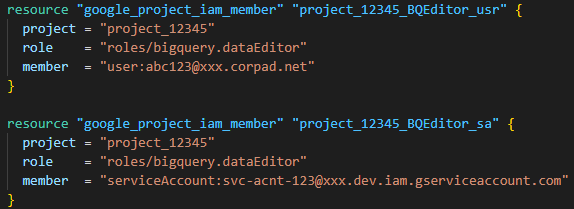
We execute code blocks like this in Terraform for access provisioning.
resource “google_project_iam_member” “project_permissions_base” {
member = “group:aad_group@mycompany.com”
project = “gcp-project”
role = “roles/bigquery.dataOwner”
}
We always review (and do peer review as well) the Terraform plan output before running the apply. There is still room for human error through. We must exercise extreme caution when it comes to IAM policies, since an unintentional destruction of these policies can result in chaos, especially in Production environment.
To address this, I developed a process to monitor Terraform deployments for any inadvertent IAM policy changes. This allows us to identify and correct any IAM policy errors before opening up the environment to users.
This process executes couple of shell scripts through GitHub Actions. The shell scripts run gcloud commands to capture the IAM policies at project level before and after apply, and compare the differences. The details are written to a GCS bucket.
Disclaimer: The posts here represent my personal views and not those of my employer or any specific vendor. Any technical advice or instructions are based on my own personal knowledge and experience.